Advanced Data Protection
Enterprise grade security.
Built from the ground up.
Your business is nobody else’s. Not even DataTools.


Encrypted
Cloud Computing™
Our most advanced cloud security architecture specifically built with enterprise in mind.

Encrypted Cloud Computing™
Cloud security at its highest.
Protections at its tightest.
We achieved this once with the launch of DataTools Kleber in the Cloud, but we weren’t content to stop there. We set out to push these boundaries even further — with a goal to handle larger batch files securely with groundbreaking speed and performance.
That led us to revisit our existing security stack and integrate additional layers for higher volume workloads. An innovative cloud security architecture purpose-built to process batch data securely at the scale today’s largest enterprises demand. We call it Encrypted Cloud Computing™.
Encrypted Cloud Computing™ builds on DataTools’ robust, industry-leading cloud security, now taken to a whole new scale. It ensures that even the most intensive batch jobs run with airtight protections. Your data remains confidential, heavily encrypted, and not accessible to anyone — not even DataTools.

Why we built it
Competing cloud environments, while convenient, pose familiar risks. Once data is inside competing cloud platforms, enforcing zero-access guarantees becomes challenging. Logging systems, privileged support consoles, and broad administrative access can inadvertently expose data or leave it vulnerable during operational troubleshooting.
That’s not acceptable for your businesses highly sensitive data. With Encrypted Cloud Computing™, we’ve taken a ground-up approach to cloud security that mirrors — and even surpasses — the standards we’ve long upheld with cloud and on-premise processing.
How it works with
DataTools Seltaris.
DataTools Seltaris is meticulously designed to protect your data at every step. Integrated into the core of our secure cloud environment, it utilises advanced encryption processes to handle your data without ever storing it unencrypted.
Thanks to DataTools Encrypted Cloud Computing™, we can securely process complex requests, ensuring that only you have access to your data. Your information remains encrypted during transit, throughout processing, and at rest, providing next-level security and peace of mind.
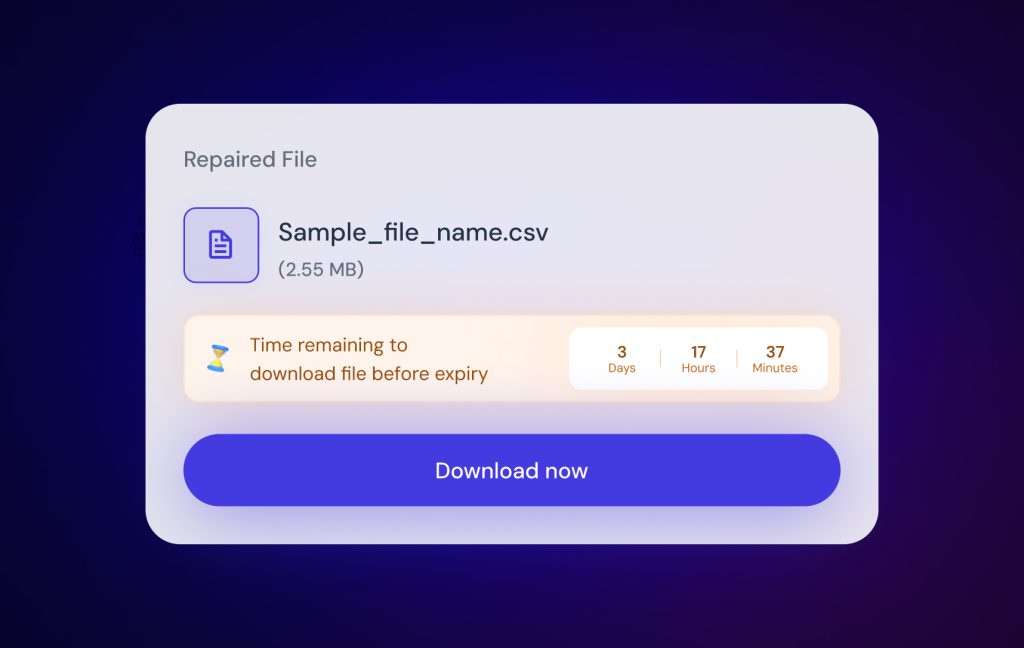
Before your Batch Process
Before your batch process begins, DataTools will provide you with a unique client secret key. This key is accessible only to you, the user; no one else, not even DataTools staff, has access to this key. It is crucial to save this key securely, as it is the only means to access your file at the end of the job.

From the Client on Up
Once you begin the job, your data file (source file) is encrypted and transmitted from your client PC to our secure cloud environment via HTTPS, ensuring it remains protected during transit.

Data Uploading via DataTools Encryption Service

DataTools Secure Cloud Repository

The Splits
Time for Processing. The DataTools Altraservice

Secure Key Management

File Merging and Result Delivery
Governance

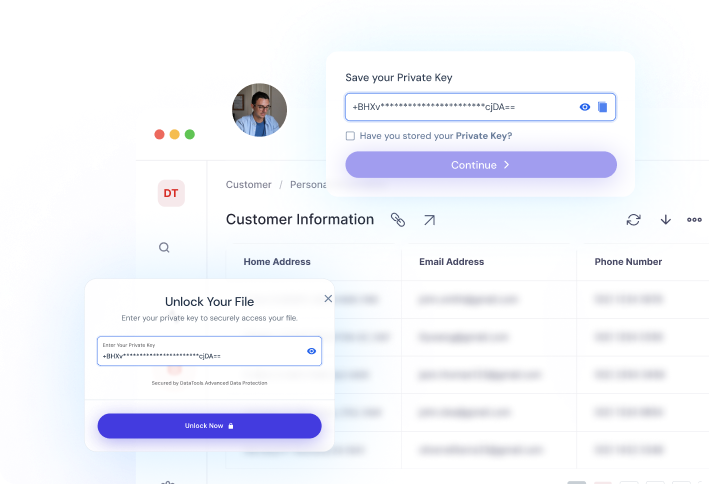
Private Keys
The single key to your encrypted result file.
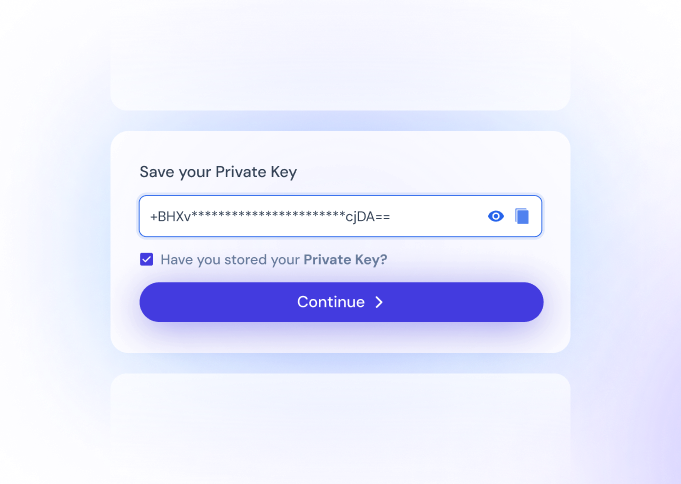


Control who sees.
By giving you sole control of your private key, Advanced data protection guarantees:
- Absolute ownership — You decide who can access your results.
- Enterprise grade security — Protections and security credentials specifically designed for the strictest compliance environments.
- Retention period — Once the retention period expires, the encrypted file is permanently erased from our severs.
With DataTools, there are no backdoors, no hidden access points, and no way for anyone else to step between you and your data. Even under force, DataTools cannot hand over what it cannot see.
That’s DataTools.
Whenever data is involved,
security is rightly a concern.



Core Features
DataTools Human Touch™
The tool is innovative.
The experience is magical.
At the core of DataTools Seltaris lies our intuitive Human Touch Technology. This powerful software features large, highly capable intelligence models specifically tailored to read and process data as efficiently as humans do.
DataTools Altraservice™
Groundbreaking Performance.
Feel the need. The need for processing speed.
Our latest step in pushing the boundaries of batch processing data, this time in the direction of fast processing speeds.

Advanced Data Protection
Enterprise grade security.
Built from the ground up.
DataTools Seltaris is meticulously designed to protect your data at every step. Integrated into the core of our secure cloud environment, it utilises advanced encryption processes to handle your data without ever storing it unencrypted.

Design made simple
Innovation for all.
The best innovations are built for everyone.
At DataTools, we have always believed that data quality software should be simple.
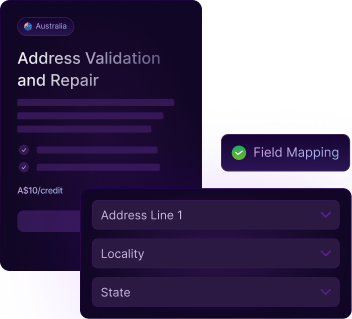
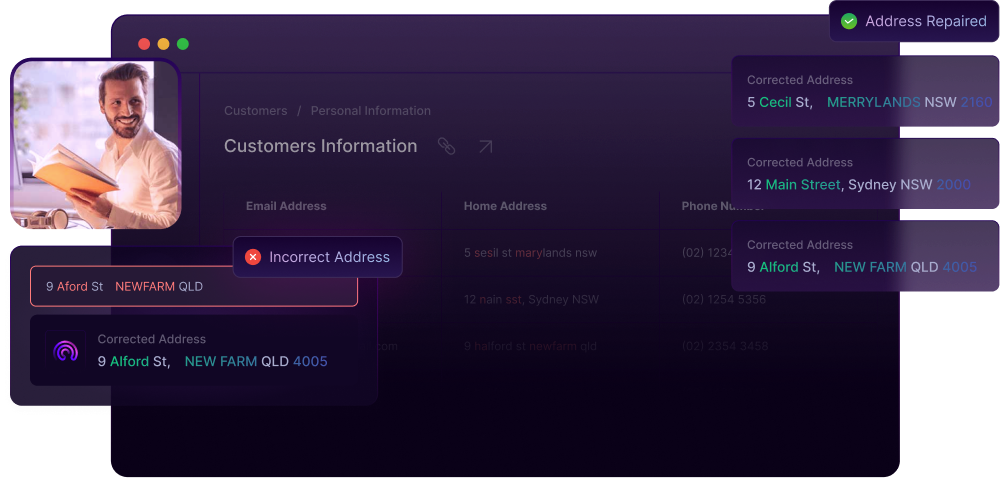
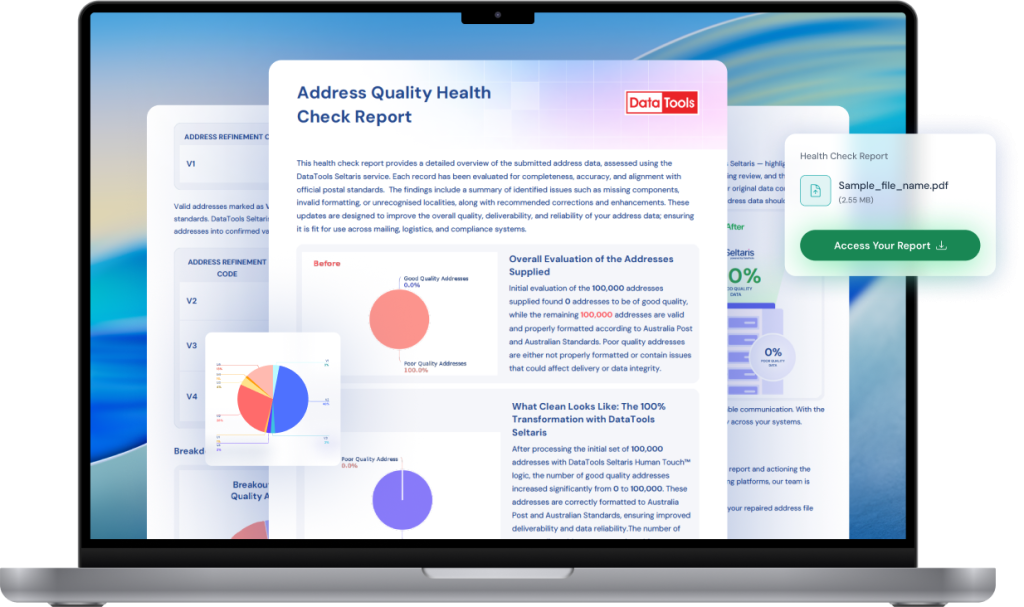
Health Check Report
Data quality at its finest detail.
This Health Check Report delivers a clear and comprehensive assessment of your submitted address data delivered in an easy to read PDF, analysed through the DataTools Seltaris service.
Bulk Data Enhancement Tool
DataTools Seltaris
High Quality Results, Unbelievable Performance. Incredibly Secure.